Key takeaways
-
Safe custody of crypto assets has become increasingly commoditised as an increasing number of regulated, reputable and resourceful institutions continue to join the space. With recent positive regulatory changes in the U.S., we expect large global custodians and banks to continue to enter the industry, further institutionalising crypto custody.
-
While these solutions are effective for custody of long-term crypto holdings, active trading strategies that aim to extract alpha from major centralised crypto exchanges or DeFi require more sophisticated solutions and setups.
-
Off-exchange settlement to allow safer access to these markets continues to evolve, albeit at a slower pace than we hoped. As of today, counterparty risk management continues to require a more complex infrastructure setup and the right processes.
-
Allocating to crypto hedge funds still requires getting comfortable with smaller teams compared with TradFi counterparts. In our view, using separately managed accounts rather than LP fund investments where appropriate can be a more controlled way of accessing these unique opportunities over time.
-
While cybersecurity risk is present in any digital activity, crypto hacks have been regular and prominent in the past. As exchanges grow and enjoy stronger capital positioning, they are increasingly well placed to withstand these incidents, as was the case recently with Bybit. Nevertheless, across the entire ecosystem, best practices must be followed and become incorporated into any fund manager’s due diligence to prevent recurrence of similar security breaches.
Introduction
The fast-paced nature of crypto often creates challenges in implementing operational best practices to mitigate against the risks that are specific to the crypto industry. Hacks, frauds and loss of private keys etc, have characterised the evolution of the space, requiring a specialised approach to assessing and implementing operational best practices.
While there is scope for further enhancements, much progress has been made in operational best practice, paving the way for institutions to adopt the new technology and gain exposure to the asset class. While simple crypto custody, and the counterparties who offer it, are now increasingly well understood, the custody requirements for more complex investment strategies in crypto markets are not as simple.
The appeal of alpha-generating opportunities offering superior returns or yields may be enticing, but it requires a good understanding of the associated risks and a clear vision on how to mitigate these. This is at the heart of how we build our multi-manager products, which the Forteus team has been doing since 2019. We share here some insights on how to address these operational challenges.
Investing with smaller teams
Many crypto managers have lower AUM than their TradFi hedge fund peers. This is partly because some of the strategies, such as market making activities, can accommodate comparatively less capacity. These strategies can nevertheless offer very attractive returns.
The implication for allocators is that they are often confronted with smaller teams, leading to limited segregation of duties in operational matters, increasing the likelihood of errors. Workarounds that we look for when assessing such funds include:
- Firms can invest in robust technological set-ups which can handle routine operational tasks such as reconciliations of internal net asset value information to the external administrators. This can reduce the need for multiple operations personnel. However, not all firms have these set-ups. As a result, we continue to drive for further investment in this area.
- Firms should leverage their service providers to mitigate risk from a lack of segregation of duties. An example includes having the fund administrator be part of the cash movement process in conjunction with internal management.
- As an alternative, firms can engage outsourced fractional COO groups that work on a part-time basis, until they have sufficient resources to afford fully-fledged operational teams. As an allocator, we are comfortable with this approach as long as there are sufficient safeguards and information barriers between the outsourced groups’ respective clients.
While we can be commercial in assessing managers with small teams, there are certain elements that we will always require before we can allocate to a fund, such as:
- An independent administrator
- Independent auditors
- Reputable service providers appropriate to the strategy
In many cases, strategies run by smaller teams may best be accessed through separately managed accounts (SMAs). Under these set-ups the allocator will utilise their own platform while the investment teams concentrate on alpha generation. This of course requires allocators to have their own custodial set-ups, access to trading venues and risk monitoring tools. While this structure allows for tighter operational control and more efficient use of capital, it is not always possible, as in some cases, the operational infrastructure itself may be integral to the manager’s edge. We therefore favour a hybrid model, taking advantage of both fund allocations as well as SMAs to access the broadest and most attractive strategies in the crypto space.
Finding the right custody model
Overview of custody solutions
The specific ways in which digital asset private keys are held are beyond the scope of this paper. At a high level, assets remain on-chain while the combination of public and private keys are held (‘custodied’) in wallets. The major wallet types are:
-
Hardware wallets: Purpose-built devices to generate and store keys on an air-gapped device. Examples include Ledger, Trezor and offline servers (where scale is required). These are generally ‘cold-storage’ in nature i.e. not connected to the internet.
-
Web wallets: that host keys via a web portal or web browser, generally saving them in an encrypted partition within the web browser files. These are ‘hot-storage’ solutions, i.e. connected to the internet, with examples including Metamask. Web wallet software often acts as a convenient interface between hardware solutions and applications on the web.
-
Software wallets: which are purpose-built applications installed on computers or mobile devices (e.g. FireBlocks) which could either be ‘hot’ or ‘cold’, or a combination thereof.
-
Custodial wallets: that are hosted by a dedicated custody service provider. Again, these could be a combination of ‘hot’- or ‘cold’-storage through either hardware wallets or software wallets. In this case, the custodian assumes the operational burden of generating, storing and maintaining the keys.
While “cold”-storage solutions are generally more secure as the risk of hacks through online attacks is considerably lower, they are nevertheless subject to other risks such as loss of keys and corruption of hardware devices. There are countless stories of early Bitcoin holders who have lost access to their assets. This is where custodial solutions can play an important role.
Selecting the right custodial solution
Ultimately, the choice of the right custodial setup is dependent on how crypto assets are used within the investment strategy. Typically, we would expect the following from our managers.
Low turnover strategies
Strategies that do not involve active trading, such as long-only, generally custody private keys in cold storage wallets with appointed custodial counterparties. While the time to withdraw assets from cold-storage wallets has fallen over time, there is scope for improvement in the operational workflows at some custodians. Managers can now choose from institutional and regulated custodians, such as Coinbase, Fidelity, Anchorage as well as crypto native counterparties like Copper and Bitgo.
Within our own liquid token fund, we use three different regulated custodians. One reason for diversifying, aside from being good practice, is to have access to custody solutions under various jurisdictions, which may have quite different regulatory frameworks for crypto custody. Over time, we would expect this to become less relevant as regulations evolve and get harmonised.
In particular, the positive change in the regulatory stance in the US should result in large US banks offering custodial services to crypto clients. The tone to restrict the provision of normal fiat banking services to crypto clients in the US is already shifting, with banks encouraged to embrace crypto clients, subject to standard risk management procedures being in place. We would not be surprised to soon see the large banks offering direct crypto custodial solutions, as crypto assets get treated like other asset classes, removing the prohibitive reserve requirements that were previously imposed on U.S. banks to do so.
Active trading strategies
Higher frequency or more active trading strategies generally require assets to be immediately available for trading. Generally, this leads to custody of private keys in a combination of ‘hot-storage’ and ‘warm-storage’ solutions, such as at Copper, as well as posting collateral directly on crypto exchanges. Leaving assets directly on crypto exchanges exposes funds to the full credit risk of the exchange. Having assets directly on exchanges needs to be managed well as in this case, assets are in commingled wallets under the full control of the relevant exchange. Regulation of exchanges is still in its infancy and the majority are licensed only to the extent of carrying out AML/KYC on their clients.
There are however ways to minimise exchange counterparty risk. In particular, off-exchange settlement arrangements such as tri-party agreements have become increasingly adopted after the FTX collapse, albeit at a slower pace than we would have hoped. We cover tri-party arrangements in the section below. When capital is directly deposited on exchanges, we expect leverage to be used to minimise assets held on exchanges, continuous monitoring of exchanges by managers, and swift action to be taken should there be cause for concern. These processes were clearly demonstrated by all of the managers we allocate to within our multi-manager product following the Bybit hack in February. All managers had withdrawn a majority of their assets from the platform within the hour.
DeFi
When it comes to strategies active in DeFi, assets will generally be deployed directly on-chain on selected protocols. Investment managers running these strategies generally use systems such as Fireblocks, Gnosis Safe, Coinbase Web3, or in some cases proprietary systems to manage the workflows. While decentralised protocols remove, to a large extent, the counterparty risk associated with centralised exchanges, they introduce new risks, such as vulnerabilities associated with smart contracts. This is in addition to the risks associated with managing the movement of assets among protocols. For strategies that are active on-chain, we expect managers to implement best practice procedures, such as the following:
-
Detailed due diligence of the systems used by appropriately qualified and knowledgeable systems specialists. The $1.4 billion hack of crypto exchange Bybit in February 2025 arose from an exploitation of the web interface of Safe (the wallet infrastructure provider used by Bybit), according to a report by the NCC Group. This highlights the importance of initial and ongoing cybersecurity assessment of third-party systems, or any vendors used by crypto managers.
-
Engagement of specialist smart contract auditors to carry out security assessments of protocols used.
-
Real-time monitoring, alert systems and fast action in the event of security breaches of protocols used.
-
Taking out insurance on the protocols where available.
Custodial counterparties have differing control processes, but good practice generally involves the following:
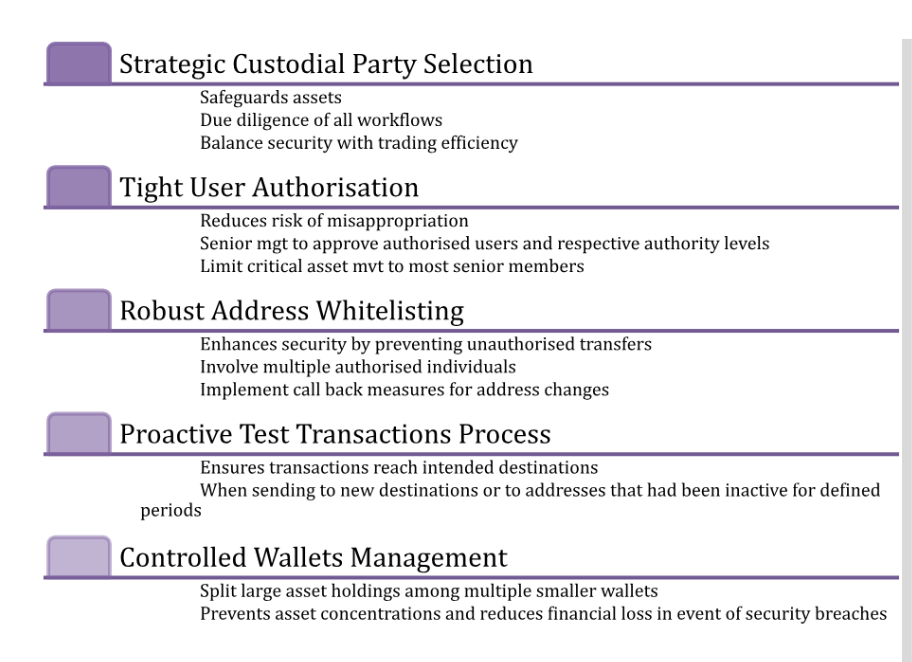
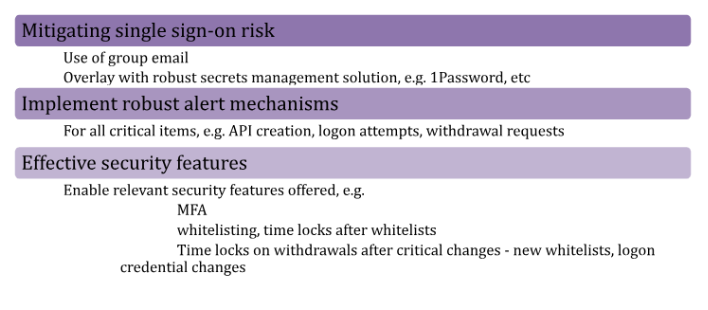
Where a fund’s collateral is held on exchanges, good practices include
Control processes over movement of cash that have been refined in TradFi are applicable equally in the sector, including involvement of multiple signatories when making cash payments.
Counterparty risk mitigation
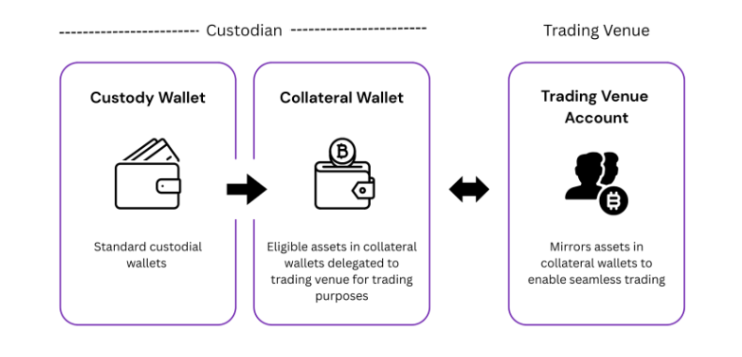
Probably the most secure way to manage exchange counterparty risk is by utilising off-exchange settlement mechanisms, such as tri-party agreements. In their simplest form, a tri-party arrangement involves a fund posting its collateral at a custodian (instead of directly on an exchange) in a way that enables the fund to trade seamlessly on an exchange, as depicted below.
The main players publicly offering such arrangements include :
-
Copper ClearLoop, while not truly 100% tri-party in that agreements are bilateral between Copper and the exchanges, and between Copper and the relevant clients, clients’ collateral is nevertheless held in trust by Copper. Copper currently enables trading on OKX, Bybit, Bit, Bitget, Deribit, Bitfinex, Gate.io and Powertrade. Copper ClearLoop also offers multi-custodial solutions through its arrangement with Komainu and BitGo.
-
Komainu Connect & OKX
-
Zodia Interchange with exchanges including Deribit, Bitfinex, LMAX and OTC desks
-
Sygnum Protect & Binance and Deribit - with one of its unique selling points being the ability to use yield-bearing collateral such as US treasuries that offsets the cost of the offering.
-
Ceffu MirroX & Binance
Factors to consider when selecting the most appropriate solutions include:
-
The number of trading counterparties available within the tri-party arrangement, and the fit with the fund’s trading strategy (this is a moving picture as many custodians are actively working on adding exchanges to their offerings);
-
The credibility of the custodian in the arrangement is essential, since this is where the collateral will sit. Important considerations include regulatory status, custodial set up (commingled vs segregated wallets for example) and the integrity of the infrastructure set up, among others.
-
The cost of the arrangement (net of any potential yield on the collateral).
-
Flexibility of the solution, particularly the ability to move capital, which can be critical for certain strategies.
While there has been a growing trend towards these arrangements following the collapse of FTX, the availability and speed of adoption has been slower than we would like to see. Some of the pain points include:
-
Complex legal negotiations, as there were no precedents in the crypto ecosystem previously
-
The arrangements can be very costly, in some cases leading custodians and exchanges to require evidence of sufficient collateral commitments ahead of implementation.
-
Low number of custodian / exchange combinations, restricting users to very limited options. As a result, some fund managers continue to hold assets directly on exchanges and mitigate exchange counterparty risk in other ways, including tight limits on concentrations.
We are clearly looking forward to more exchanges making their venues accessible through such solutions and would of course like to see more custodian-exchange pairings to reduce the number of custodians that a fund has to engage with.
Hacks and cybersecurity
Cybersecurity will always be a critical component of any organisation, and more so for participants in the crypto ecosystem given that the asset class is digitally native. At the enterprise level, standards have evolved over the past two decades and good practices include:
- Access controls such as multi-factor authentication, password policies and user authorisations
- Standard cyber defenses such as firewalls, malware, anti-virus, etc
- Continuous vulnerability scanning
- Cybersecurity awareness training - staff often represent the weakest link
- Audits of the infrastructure security set-up by specialist external parties
We note above that humans (staff) are the weakest link in any cyber security set-up. As a result, ongoing cyber awareness should be a core element to the security framework of any firm. In the Bybit hack referenced above, the attackers used sophisticated social engineering techniques to fool Bybit authorised approvers (3 approvers according to reports) into believing they were approving a genuine transaction.
Better vulnerability detection mechanisms especially at Safe (where the attackers are reported to have compromised a developer’s machine) could have alerted responsible individuals or systems at Safe to disable the attack.
Additional hygiene factors that we like to see implemented and that can prevent similar attacks or limit their impacts include:
- Enabling all the security features on exchange accounts, including delays for sending assets to newly whitelisted addresses, as outlined in the ‘Custody’ section above.
- Extra safety measures for movements above a set threshold, e.g. to allow for other approval forms, such as phone calls / callbacks, before approval on portals
- Splitting of assets into a larger number of smaller wallets as outlined in the ‘Custody’ section above.
Conclusion
To further adapt and prepare the ecosystem for wider institutional participation, we will continue to advocate for the following improvements:
- Continued investment in the operational infrastructure of crypto hedge funds, including extensive use of appointed service providers as appropriate;
- Expanded adoption of the tri-party off-exchange settlement by all the major centralised trading venues in an effort to mitigate exchange counterparty risk;
- Better clarity on the AML / KYC / KYT status of major DeFi trading protocols in an effort to attract institutional capital; and
- Entry of large, well-capitalised firms into the crypto ecosystem, particularly in the areas of trading and prime brokerage to complement the trend already underway in custody.